Aws Cloudformation Sqs Lambda Trigger
Simple example template for lambda trigger whe event published on SQS queue.
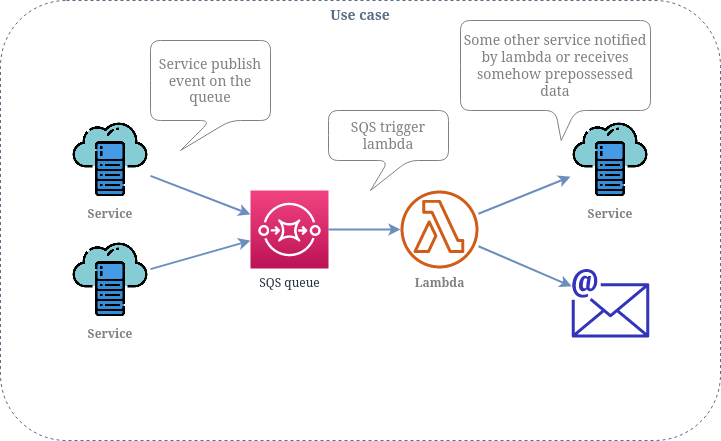
Use case
Simple use case when system is expected to react on SQS event and somehow process the data or perform an action.
Resources diagram
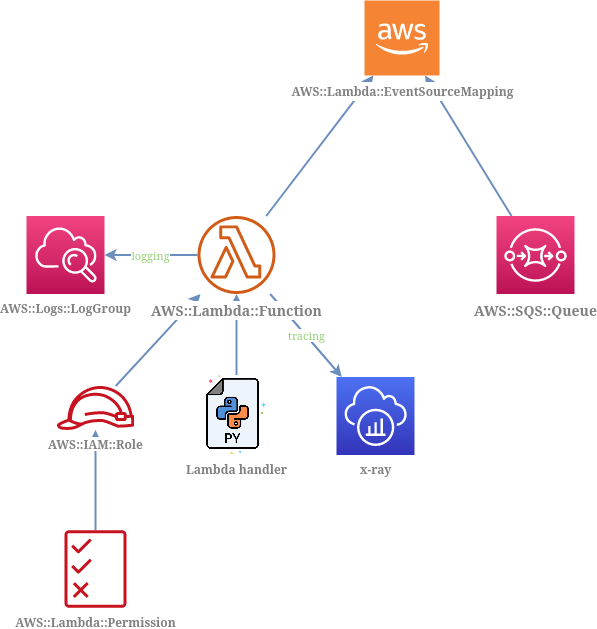
Cloudformation
Event source
Allow trigger specified lambda by defined event source mapping
WsEgressLambdaSourceMapping:
Type: 'AWS::Lambda::EventSourceMapping'
DependsOn:
- SimpleQueue
- SimpleLambda
Properties:
BatchSize: 5 # maximum number of items to retrieve in a single batch
Enabled: true
EventSourceArn: !GetAtt SimpleQueue.Arn
FunctionName: !GetAtt SimpleLambda.ArnQueue configuration
In this setup, event can remain in queue up to 4 days, and will be invisible for other listeners up to 30 seconds.
SimpleQueue:
Type: 'AWS::SQS::Queue'
Properties:
QueueName: !Sub '${Env}-queue'
DelaySeconds: 0
MaximumMessageSize: 262144
MessageRetentionPeriod: 345600 ## 4 days
VisibilityTimeout: 30 ## secondsTemplate
AWSTemplateFormatVersion: '2010-09-09'
Description: 'Simple SQS lambda trigger.'
Parameters:
Env:
Type: 'String'
Description: 'Logical environment dev|test etc'
Resources:
SimpleQueue:
Type: 'AWS::SQS::Queue'
Properties:
QueueName: !Sub '${Env}-queue'
DelaySeconds: 0
MaximumMessageSize: 262144
MessageRetentionPeriod: 345600 ## 4 days
VisibilityTimeout: 30 ## seconds
SimpleLambdaLogGroup:
Type: 'AWS::Logs::LogGroup'
Properties:
LogGroupName: !Sub '/aws/lambda/${Env}-simple-lambda'
RetentionInDays: 3
SimpleLambdaRole:
Type: 'AWS::IAM::Role'
DependsOn:
- SimpleQueue
Properties:
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
Service:
- lambda.amazonaws.com
Action:
- sts:AssumeRole
Policies:
- PolicyName: !Sub '${Env}-simple-lambda'
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- logs:CreateLogStream
- logs:PutLogEvents
Resource: !Sub 'arn:${AWS::Partition}:logs:${AWS::Region}:${AWS::AccountId}:log-group:/aws/lambda/${Env}-simple-lambda:*:*'
- Effect: Allow
Action:
- sqs:ReceiveMessage
- sqs:DeleteMessage
- sqs:GetQueueAttributes
- sqs:ChangeMessageVisibility
Resource: !GetAtt SimpleQueue.Arn
- Effect: Allow
Action:
- xray:PutTraceSegments
- xray:PutTelemetryRecords
Resource: '*'
WsEgressLambdaSourceMapping:
Type: 'AWS::Lambda::EventSourceMapping'
DependsOn:
- SimpleQueue
- SimpleLambda
Properties:
BatchSize: 5
Enabled: true
EventSourceArn: !GetAtt SimpleQueue.Arn
FunctionName: !GetAtt SimpleLambda.Arn
SimpleLambda:
Type: 'AWS::Lambda::Function'
DependsOn:
- SimpleLambdaRole
- SimpleLambdaLogGroup
Properties:
Description: 'SQS triggered lambda.'
FunctionName: !Sub '${Env}-simple-lambda'
Handler: index.handler
Runtime: python3.7
MemorySize: 128
Timeout: 30
TracingConfig:
Mode: Active
Role: !GetAtt SimpleLambdaRole.Arn
Code:
ZipFile: |
import os
import json
def handler(event, context):
print("Event: {}".format(event))