Aws Cloudformation S3 Lambda Trigger
Simple example template for s3 lambda trigger whe new object added
Use case
Simple use case when user or service put document to s3 bucket and system is expected to react on that event and somehow process the data.
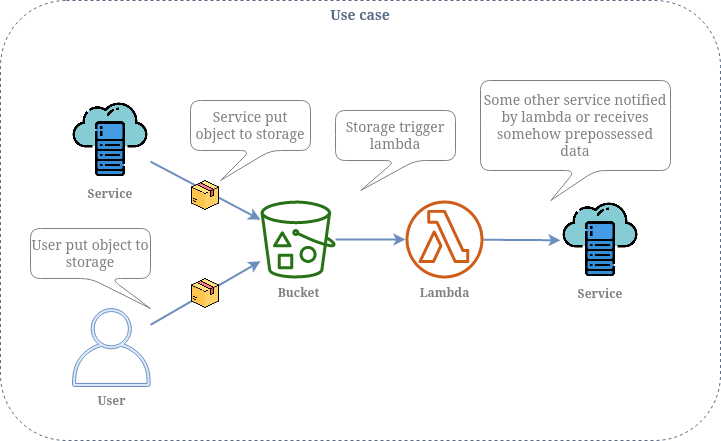
Resources diagram

Cloudformation
Permissions
Allow trigger specified lambda by defined s3 bucket
TriggerLambdaPermission:
Type: AWS::Lambda::Permission
Properties:
Action: 'lambda:InvokeFunction'
FunctionName: !Ref SimpleLambda
Principal: s3.amazonaws.com
SourceArn: !Sub 'arn:aws:s3:::${Env}-simple-bucket'
SourceAccount: !Ref AWS::AccountIdBucket configuration
In this case lambda will be triggered by any upload of files with suffics ‘.csv’ into any ‘folder’ in the bucket. In order to capture by specific keys, prefix should be provided.
NotificationConfiguration:
LambdaConfigurations:
- Event: s3:ObjectCreated:*
Function: !GetAtt SimpleLambda.Arn
Filter:
S3Key:
Rules:
- Name: suffix
Value: .csvTemplate
AWSTemplateFormatVersion: '2010-09-09'
Description: 'Simple s3 lambda trigger.'
Parameters:
Env:
Type: 'String'
Description: 'Logical environment dev|test etc'
Resources:
SimpleBucket:
DependsOn:
- SimpleLambda
- TriggerLambdaPermission
Type: AWS::S3::Bucket
Properties:
BucketName: !Sub '${Env}-simple-bucket'
BucketEncryption:
ServerSideEncryptionConfiguration:
- ServerSideEncryptionByDefault:
SSEAlgorithm: AES256
VersioningConfiguration:
Status: Enabled
LifecycleConfiguration:
Rules:
- Id: 'StandardIA'
Status: Enabled
Transitions:
- StorageClass: STANDARD_IA
TransitionInDays: '30'
NotificationConfiguration:
LambdaConfigurations:
- Event: s3:ObjectCreated:*
Function: !GetAtt SimpleLambda.Arn
Filter:
S3Key:
Rules:
- Name: suffix
Value: .csv
TriggerLambdaPermission:
Type: AWS::Lambda::Permission
Properties:
Action: 'lambda:InvokeFunction'
FunctionName: !Ref SimpleLambda
Principal: s3.amazonaws.com
SourceArn: !Sub 'arn:aws:s3:::${Env}-simple-bucket'
SourceAccount: !Ref AWS::AccountId
SimpleLambdaLogGroup:
Type: 'AWS::Logs::LogGroup'
Properties:
LogGroupName: !Sub '/aws/lambda/${Env}-simple-lambda'
RetentionInDays: 30
SimpleLambdaRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
Service:
- lambda.amazonaws.com
Action:
- 'sts:AssumeRole'
Policies:
- PolicyName: !Sub '${Env}-simple-lambda'
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- 'logs:CreateLogStream'
- 'logs:PutLogEvents'
Resource: !Sub 'arn:${AWS::Partition}:logs:${AWS::Region}:${AWS::AccountId}:log-group:/aws/lambda/${Env}-simple-lambda:*:*'
- Effect: Allow
Action:
- 'xray:PutTraceSegments'
- 'xray:PutTelemetryRecords'
Resource: '*'
SimpleLambda:
DependsOn:
- SimpleLambdaRole
- SimpleLambdaLogGroup
Type: 'AWS::Lambda::Function'
Properties:
Description: 'Lambda triggered by s3'
FunctionName: !Sub '${Env}-simple-lambda'
Handler: index.handler
Runtime: python3.7
MemorySize: 256
Timeout: 30
TracingConfig:
Mode: Active
Role: !GetAtt SimpleLambdaRole.Arn
Code:
ZipFile: |
import os
def handler(event, context):
print("Event: {}".format(event))
# Some logic here