Aws Cloudformation IAM User
Simple example of IAM user creation via Cloudformation with defined group and policies.
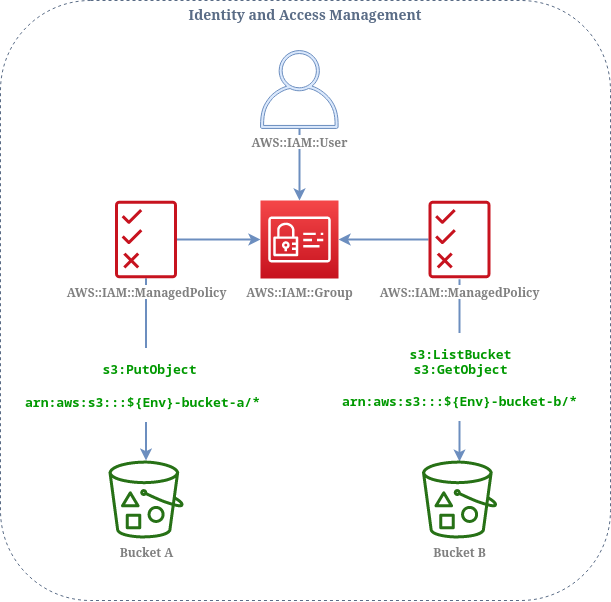
Resources diagram
Users can be assigned to a group with defined list of permissions to resources (S3, DynamoDB, SNS, SQS etc).
Cloudformation
Base
Template with stack parameters
AWSTemplateFormatVersion: '2010-09-09'
Description: 'IAM User with S3 access.'
Parameters:
Env:
Type: 'String'
Description: 'Environment name (String parameter dev|test etc).'Managed policies
Allow put objects into bucket (containing environment parameter in it’s name)
PermissionsBucketA:
Type: 'AWS::IAM::ManagedPolicy'
Properties:
ManagedPolicyName: 'permissions.bucket.a'
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: 'Allow'
Action:
- 's3:PutObject'
Resource:
- !Sub 'arn:aws:s3:::${Env}-bucket-a/*'Allow list and get objects from bucket
PolicyBucketB:
Type: AWS::IAM::ManagedPolicy
Properties:
ManagedPolicyName: !Sub '${Env}.policy.bucket.b'
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: 'Allow'
Action:
- 's3:ListBucket'
Resource:
- !Sub 'arn:aws:s3:::${Env}-bucket-b/*'
- Effect: 'Allow'
Action:
- 's3:GetObject'
Resource:
- !Sub 'arn:aws:s3:::${Env}-bucket-b/*'Group
A group containing policies. Also depends on them to be created first.
SimpleGroup:
DependsOn:
- PolicyBucketA
- PolicyBucketB
Type: 'AWS::IAM::Group'
Properties:
GroupName: !Sub '${Env}-simple-group'
ManagedPolicyArns:
- Ref: PolicyBucketA
- Ref: PolicyBucketBUser
Simple user with reference to group we want to assign him to.
SimpleUser:
DependsOn: SimpleGroup
Type: 'AWS::IAM::User'
Properties:
UserName: !Sub '${Env}.simple.user'
Groups:
- !Ref SimpleGroupComplete template
AWSTemplateFormatVersion: '2010-09-09'
Description: 'Example IAM user with s3 access.'
Parameters:
Env:
Type: 'String'
Description: 'Environment name (String parameter dev|test etc).'
Resources:
PolicyBucketA:
Type: 'AWS::IAM::ManagedPolicy'
Properties:
ManagedPolicyName: !Sub '${Env}.policy.bucket.a'
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: 'Allow'
Action:
- 's3:PutObject'
Resource:
- !Sub 'arn:aws:s3:::${Env}-bucket-a/*'
PolicyBucketB:
Type: AWS::IAM::ManagedPolicy
Properties:
ManagedPolicyName: !Sub '${Env}.policy.bucket.b'
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: 'Allow'
Action:
- 's3:ListBucket'
Resource:
- !Sub 'arn:aws:s3:::${Env}-bucket-b/*'
- Effect: 'Allow'
Action:
- 's3:GetObject'
Resource:
- !Sub 'arn:aws:s3:::${Env}-bucket-b/*'
SimpleGroup:
DependsOn:
- PolicyBucketA
- PolicyBucketB
Type: 'AWS::IAM::Group'
Properties:
GroupName: !Sub '${Env}-simple-group'
ManagedPolicyArns:
- Ref: PolicyBucketA
- Ref: PolicyBucketB
SimpleUser:
DependsOn: SimpleGroup
Type: 'AWS::IAM::User'
Properties:
UserName: !Sub '${Env}.simple.user'
Groups:
- !Ref SimpleGroup